When deploying a new application or service, security is always a top concern. The internet is full of malicious actors probing applications for vulnerabilities and sniffing for open ports. Tools like iptables are essential to any developer’s toolkit, but they can be complicated to use, especially when building distributed services. Adding a new Droplet can require updating your configuration across all of your infrastructure.
At DigitalOcean, we are working to make it easier for developers to build applications and deploy them to the cloud by simplifying the infrastructure experience. Today, we’re excited to bring that approach to security with Cloud Firewalls, an easily configurable service for securing your Droplets. It is free to use and designed to scale with you as you grow.
By using Cloud Firewalls, you will have a central location to define access rules and apply them to all of your Droplets. We enforce these rules on our network layer. Unauthorized traffic will not reach your Droplets, and this protection doesn’t consume any resources from your Droplet.
Secure by Default
When using Firewalls, we start from the principle of least privilege—only the ports and IPs explicitly defined by you will be accessible. Any packet that doesn’t fit the rules will be dropped before it reaches your Droplet. A simple Firewall that would only allow HTTP, SSH, and ICMP connections from any source would need three rules:

If someone tried to access this Droplet on any other port—say FTP using port 21—they would receive a timeout because Firewalls filtered out the traffic.
Easy to Configure
We’ve designed Firewalls to be easy to configure. Your source and destination rules can specify individual Droplets by name, Load Balancers, IP ranges, and even sets of Droplets by using Tags.

For finer-grained control, you can also apply multiple Firewalls to a Droplet. This allows you to keep rules for different concerns in different Firewalls. For example, you could create one Firewall called webapp-firewall, that allows only HTTP on port 80, and another called admin-firewall, that allows SSH and ICMP from only a specific IP. Our service will combine their rules and enforce them together.
Beyond the Control Panel, you can manage your Firewalls on the command line with doctl or automate using our RESTful API or our Go and Ruby API client libraries. Expect more integrations to come along soon, thanks to our amazing community.
Works at Scale
Even without automation, Firewalls makes it much easier to secure distributed applications with large numbers of resources. You can leverage tagging to group and organize any number of Droplets, and use them to define how each group of Droplets is secured by Firewalls.
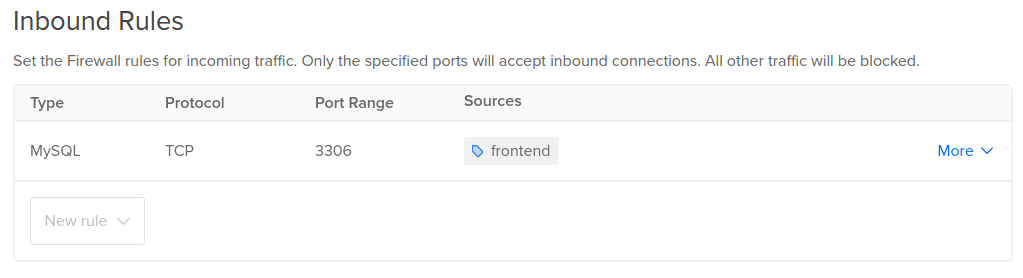
For example, you could create a Firewall called db-firewall and only allow inbound connections from all Droplets tagged frontend, securing your database from unauthorized access. If you add this tag to more Droplets, they will automatically be recognized by our system and be whitelisted by this rule.
Getting Started
Whether you’re ready to dive in and create your first Firewall or you just want to learn more, check out these tutorials on our Community site for all the details and some best practices:
- How to Create Your First DigitalOcean Firewall
- An Introduction to DigitalOcean Firewalls
- How to Organize DigitalOcean Firewalls
We can’t wait to hear your feedback. It helps guide us as we continue to work on making your infrastructure more secure and easier to manage at scale. Let us know what you think in the comments below, and stay tuned for major network security improvements later this year.
About the author
Try DigitalOcean for free
Click below to sign up and get $200 of credit to try our products over 60 days!Related Articles

Native .NET Buildpack Support is Now Available on App Platform
- March 5, 2026
- 2 min read

Supabase Template is Now Available on DigitalOcean App Platform
- February 26, 2026
- 3 min read

Expanding our Agentic Inference Cloud: Introducing GPU Droplets Powered by AMD Instinct™ MI350X GPUs
- February 19, 2026
- 2 min read