- Log in to:
- Community
- DigitalOcean
- Sign up for:
- Community
- DigitalOcean
By Savic and Rachel Lee
Not using Ubuntu 22.04?
Choose a different version or distribution.
The author selected the Free and Open Source Fund to receive a donation as part of the Write for DOnations program.
Introduction
Postfix is a mail transfer agent (MTA), an application used to send and receive email. It can be configured so that it can be used to send emails by local application only. This is useful in situations when you need to regularly send email notifications from your apps or have a lot of outbound traffic that a third-party email service provider won’t allow. It’s also a lighter alternative to running a full-blown SMTP server, while retaining the required functionality.
In this tutorial, you’ll install and configure Postfix as a send-only SMTP server. You’ll also request free TLS certificates from Let’s Encrypt for your domain and encrypt the outbound emails using them.
Note: As of June 22, 2022, DigitalOcean is blocking SMTP for all new accounts. As a part of this new policy, we have partnered with SendGrid so our customers can still send emails with ease. You can learn more about this partnership and get started using SendGrid by checking out our DigitalOcean’s SendGrid Marketplace App.
Prerequisites
- One Ubuntu 22.04 server set up with the Initial Server Setup with Ubuntu 22.04, including creating a sudo non-root user.
- A fully registered domain name. This tutorial will use
your_domainthroughout. You can purchase a domain name on Namecheap, get one for free on Freenom, or use the domain registrar of your choice. - An A DNS record with
your_domainpointing to your server’s public IP address. You can follow this introduction to DigitalOcean DNS for details on how to add them.
Note: Your server’s hostname and your Droplet’s name must match your_domain, because DigitalOcean automatically sets PTR records for the Droplet’s IP address according to its name.
You can verify the server’s hostname by typing hostname at the command prompt. The output should match the name you gave the Droplet when it was being created. If it’s not correct, run the following command to set it:
- hostname your_domain
Additionally, your account must have port 25 enabled, which may not be the case for some accounts. Do note that some email providers may reject email coming from DigitalOcean (or other) IP ranges, at their own discretion.
Step 1 — Installing Postfix
In this step, you’ll install Postfix. The fastest way is to install the mailutils package, which bundles Postfix with a few supplementary programs that you’ll use to test sending email.
First, update the package database:
- sudo apt update
Then, install Postfix by running the following command:
- sudo apt install mailutils
Near the end of the installation process, you will be presented with the Postfix configuration window:
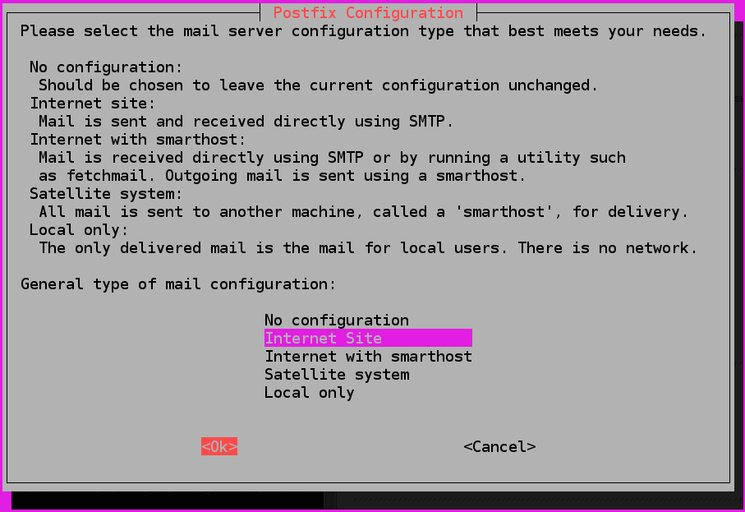
The default option is Internet Site. That’s the recommended option for your use case, so press TAB, and then ENTER. If you only see the description text, press TAB to select OK, then ENTER.
If it does not show up automatically, run the following command to start it:
- sudo dpkg-reconfigure postfix
After that, you’ll get another configuration prompt regarding the System mail name:
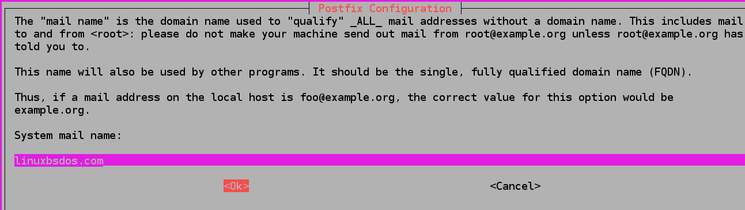
The System mail name must be the same as the name you assigned to your server when you were creating it. When you’ve finished, press TAB, followed by ENTER.
You have now installed Postfix and are ready to start configuring it.
Step 2 — Configuring Postfix
In this step, you’ll configure Postfix to send and receive emails only from the server on which it is running—that is, from localhost.
For that to happen, you need to configure Postfix to listen only on the loopback interface, the virtual network interface that the server uses to communicate internally. To make the changes, you’ll need to edit the main Postfix configuration file called main.cf, stored under etc/postfix.
Open it for editing using nano or your favorite text editor:
- sudo nano /etc/postfix/main.cf
Find the following lines:
. . .
mailbox_size_limit = 0
recipient_delimiter = +
inet_interfaces = all
. . .
Set the value of the inet_interfaces setting to loopback-only:
. . .
mailbox_size_limit = 0
recipient_delimiter = +
inet_interfaces = loopback-only
. . .
If your domain is actually a subdomain and you want the email messages to look as if they were sent from the main domain, you can add the following line to the end of main.cf:
...
masquerade_domains = your_main_domain
The optional masquerade_domains setting specifies the domain for which the subdomain will be stripped off in the email address.
When you are done, save and close the file.
Then, restart Postfix by running the following command:
- sudo systemctl restart postfix
You’ve configured Postfix to only send emails from your server. You’ll now test it by sending an example message to an email address.
Step 3 — Testing the SMTP Server
In this step, you’ll test whether Postfix can send emails to an external email account using the mail command, which is part of the mailutils package that you installed in the first step.
To send a test email, run the following command:
- echo "This is the body of the email" | mail -s "This is the subject line" your_email_address
You can change the body and the subject of the email to your liking. Remember to replace your_email_address with a valid email address that you can access.
Now, check the email address to which you sent this message. You should see the message in your inbox. If it’s not there, check your spam folder. At this point, all emails you send are unencrypted, which makes service providers think it’s likely spam. You’ll set up encryption later, in step 5.
If you receive an error from the mail command, or you haven’t received a message after a prolonged period of time, check that the Postfix configuration you edited is valid and that your server’s name and hostname are set to your domain.
Note that with this configuration, the address in the From field for the test emails you send will be in the form of your_user_name@your_domain, where your_user_name is the username of the server user you ran the command as.
You have now sent an email from your server and verified that it’s successfully received. In the next step, you’ll set up email forwarding for root.
Step 4 — Forwarding System Mail
In this step, you’ll set up email forwarding for user root, so that system-generated messages sent to it on your server get forwarded to an external email address.
The /etc/aliases file contains a list of alternate names for email recipients. Open it for editing:
- sudo nano /etc/aliases
In its default state, it looks like this:
# See man 5 aliases for format
postmaster: root
The only directive present specifies that system-generated emails are sent to root.
Add the following line to the end of the file:
...
root: your_email_address
With this line, you specify that emails sent to root will be forwarded to an email address. Remember to replace your_email_address with your personal email address. When you are done, save and close the file.
For the change to take effect, run the following command:
- sudo newaliases
Running newaliases will build up a database of aliases that the mail command uses, which are taken from the config file you just edited.
Test that sending emails to root works by running:
- echo "This is the body of the email" | mail -s "This is the subject line" root
You should receive the email at your email address. If it’s not there, check your spam folder.
In this step, you set up forwarding system-generated messages to your email address. You’ll now enable message encryption, so that all emails your server sends are immune to tampering in transit and will be viewed as more legitimate.
Step 5 — Enabling SMTP Encryption
You’ll now enable SMTP encryption by requesting a free TLS certificate from Let’s Encrypt for your domain (using Certbot) and configuring Postfix to use it when sending messages.
Ubuntu includes Certbot in their default package repositories, so you can install it by running the following command:
- sudo apt install certbot
When asked for confirmation, type Y and press enter.
As part of the initial server setup in the prerequisites, you installed ufw, the uncomplicated firewall. You’ll need to configure it to allow the HTTP port 80, so that domain verification can be completed. Run the following command to enable it:
- sudo ufw allow 80
The output will look like this:
OutputRule added
Rule added (v6)
Now that the port is open, run Certbot to get a certificate:
- sudo certbot certonly --standalone --rsa-key-size 4096 --agree-tos --preferred-challenges http -d your_domain
This command orders Certbot to issue certificates with an RSA key size of 4096 bits, to run a temporary standalone web server (--standalone) for verification, and to check via port 80 (--preferred-challenges http). Remember to replace your_domain with your domain before running the command, and enter your email address when prompted.
The output will be similar to this:
OutputSaving debug log to /var/log/letsencrypt/letsencrypt.log
Requesting a certificate for aleksasavic.com
Successfully received certificate.
Certificate is saved at: /etc/letsencrypt/live/your_domain/fullchain.pem
Key is saved at: /etc/letsencrypt/live/your_domain/privkey.pem
This certificate expires on 2022-07-04.
These files will be updated when the certificate renews.
Certbot has set up a scheduled task to automatically renew this certificate in the background.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
If you like Certbot, please consider supporting our work by:
* Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
* Donating to EFF: https://eff.org/donate-le
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
As written in the notes, your certificate and private key file were saved under /etc/letsencrypt/live/your_domain.
Now that you have your certificate, open main.cf for editing:
- sudo nano /etc/postfix/main.cf
Find the following section:
# TLS parameters
smtpd_tls_cert_file=/etc/ssl/certs/ssl-cert-snakeoil.pem
smtpd_tls_key_file=/etc/ssl/private/ssl-cert-snakeoil.key
smtpd_tls_security_level=may
smtp_tls_CApath=/etc/ssl/certs
smtp_tls_security_level=may
smtp_tls_session_cache_database = btree:${data_directory}/smtp_scache
Modify it to look like this, replacing your_domain with your domain where necessary. This will update your TLS settings for Postfix:
# TLS parameters
smtpd_tls_cert_file=/etc/letsencrypt/live/your_domain/fullchain.pem
smtpd_tls_key_file=/etc/letsencrypt/live/your_domain/privkey.pem
smtpd_tls_security_level=may
smtp_tls_CApath=/etc/ssl/certs
smtp_tls_security_level=may
smtp_tls_session_cache_database = btree:${data_directory}/smtp_scache
Once you’re done, save and close the file.
Apply the changes by restarting Postfix:
- sudo systemctl restart postfix
Now, try sending an email again:
- echo "This is the body of an encrypted email" | mail -s "This is the subject line" root
Then, check the email address you provided. It’s possible that you’ll see the message in your inbox immediately because email providers are much more likely to mark unencrypted messages as spam.
You can check the technical info about the email message in your client to see that the message is indeed encrypted.
Conclusion
You now have a send-only email server, powered by Postfix. Encrypting all outgoing messages is an effective first step to email providers not marking your messages as spam outright. If you are doing this in a development scenario, then this measure should be enough.
However, if your use case is to send emails to potential site users (such as confirmation emails for a message board sign-up) or popular email providers, such as Gmail, look into setting up SPF records, so that your server’s emails are even more likely to be seen as legitimate.
Thanks for learning with the DigitalOcean Community. Check out our offerings for compute, storage, networking, and managed databases.
About the author(s)
Expert in cloud topics including Kafka, Kubernetes, and Ubuntu.
Still looking for an answer?
This textbox defaults to using Markdown to format your answer.
You can type !ref in this text area to quickly search our full set of tutorials, documentation & marketplace offerings and insert the link!
I would like to use this to connect to my domain mail.in****.co.za with my email address. I dont see any where i can enter my actual domain email username and password so postfix can connect and send from my real email.
my email client is setup as the smtp server(mail.in****.co.za)with port 587. i would like to setup postfix so instead of my client connecting to mail.in***.co.za is conntect to 192.168.8.2(postfix server)and postfix then sends email from mail.in****.co.za with my login details.
is this possible? I am busy learning postfix
Hi, I’ve followed your article and configured postfix on Ubuntu 22.04. But, when I try to test with the following command: echo “This is the body of the email” | mail -s “This is the subject line” myemail@yahoo.com
I get errors on /var/log/mail.log:
Oct 12 04:32:42 ip-172-31-2-101 postfix/anvil[88609]: statistics: max connection rate 1/60s for (smtp:133.144.233.206) at Oct 12 04:29:22 Oct 12 04:32:42 ip-172-31-2-101 postfix/anvil[88609]: statistics: max connection count 1 for (smtp:133.144.233.206) at Oct 12 04:29:22 Oct 12 04:32:42 ip-172-31-2-101 postfix/anvil[88609]: statistics: max cache size 1 at Oct 12 04:29:22 Oct 12 04:33:53 ip-172-31-2-101 postfix/pickup[87341]: 39EFF17C363: uid=1000 from=ubuntu@mydomain.com Oct 12 04:33:53 ip-172-31-2-101 postfix/cleanup[88723]: 39EFF17C363: message-id=20221012043353.39EFF17C363@ip-172-31-2-101.ap-west-2.compute.internal Oct 12 04:33:53 ip-172-31-2-101 postfix/qmgr[87340]: 39EFF17C363: from=ubuntu@mydomain.com, size=435, nrcpt=1 (queue active)
Can you give suggestions how I can fix this kind of issue? Thank you.
I am getting the following when I try and do the encryption step
Certbot failed to authenticate some domains (authenticator: standalone). The Certificate Authority reported these problems: Domain: mydomain.com Type: unauthorized Detail: 2606:xxxx:xxxx::xxxx:835: Invalid response from http://mydomain.com/.well-known/acme-challenge/3vHyvxxxxxxxxxxxxyZCgQvs: 403
Hint: The Certificate Authority failed to download the challenge files from the temporary standalone webserver started by Certbot on port 80. Ensure that the listed domains point to this machine and that it can accept inbound connections from the internet.
Do I need to setup port forwarding on my router to point port 80 to the IP of my postfix machine?
And if so, once installed, can I remove it?
Hi, i made it!!! And really works, i made the spf record to sen mail and gmail receives!!! Of course in spam folder, then i have 2 questions: How can i send mail from another machine when i already configure the server like this steps? How can I prevent sent emails from reaching the spam folder?
Whats the point ? SMTP is blocked… and “we have partnered with SendGrid so our customers can still send emails with ease” yea forgot to mention that this is not a free service…
The smtpd_*-commands where you specify certificates are only used when receiving emails so this step is kind of pointless, is it not?
- Table of contents
- Prerequisites
- Step 1 — Installing Postfix
- Step 2 — Configuring Postfix
- Step 3 — Testing the SMTP Server
- Step 4 — Forwarding System Mail
- Step 5 — Enabling SMTP Encryption
- Conclusion
Deploy on DigitalOcean
Click below to sign up for DigitalOcean's virtual machines, Databases, and AIML products.
Become a contributor for community
Get paid to write technical tutorials and select a tech-focused charity to receive a matching donation.
DigitalOcean Documentation
Full documentation for every DigitalOcean product.
Resources for startups and AI-native businesses
The Wave has everything you need to know about building a business, from raising funding to marketing your product.
Get our newsletter
Stay up to date by signing up for DigitalOcean’s Infrastructure as a Newsletter.
New accounts only. By submitting your email you agree to our Privacy Policy
The developer cloud
Scale up as you grow — whether you're running one virtual machine or ten thousand.
Get started for free
Sign up and get $200 in credit for your first 60 days with DigitalOcean.*
*This promotional offer applies to new accounts only.
