- Log in to:
- Community
- DigitalOcean
- Sign up for:
- Community
- DigitalOcean
By Elliot Cooper and Caitlin Postal

The author selected the Open Internet/Free Speech Fund to receive a donation as part of the Write for DOnations program.
Introduction
Jitsi Meet is an open-source video-conferencing application based on WebRTC. A Jitsi Meet server provides multi-person video conference rooms that you can access using with just your browser while providing comparable functionality to a Zoom or Skype conference call. The benefit of a Jitsi conference is that all your data only passes through your server. The end-to-end TLS encryption ensures that no one can snoop on the call. With Jitsi, you can ensure that your private information stays that way.
In this tutorial, you will install and configure a Jitsi Meet server on Ubuntu 22.04. The default Jitsi configuration allows anyone who can browse the server to create a new conference room, which is not ideal for a publicly available server on the internet. You will also configure Jitsi Meet so that only registered users can create new conference rooms. After creating the conference room, anyone can join it if they have the unique address and optional password.
Prerequisites
Before you begin this guide, you will need the following:
- One Ubuntu 22.04 server with a non-root sudo-enabled user and a firewall, which you can set up by following the Initial Server Setup with Ubuntu 22.04. The size of the server you need will depend on the available bandwidth and the number of participants you expect to in the conferences. The table below will give you an idea of what is required.
- A domain name configured to point to your server. Use the DNS Quickstart Guide to point domains to DigitalOcean servers. This guide uses the example domain name
jitsi.your_domain.
When choosing a server to run your Jitsi Meet instance, you need to consider the system resources for hosting conference rooms. The following benchmark information was collected from a single-core virtual machine using high-quality video settings:
| CPU | Server Bandwidth | |
|---|---|---|
| Two Participants | 5% | 30Kbps Up, 100Kbps Down |
| Three Participants | 15% | 5Mbps Up, 3Mbps Down |
The jump in resource use between two and three participants is because Jitsi will route the call data directly between the clients when there are two of them. Call data is routed through the Jitsi Meet server when more than two clients are present.
Log in to your server as the non-root, sudo-enabled user before starting Step 1.
Step 1 — Setting the System Hostname
In this step, you will change the system’s hostname to match the domain name you intend to use for your Jitsi Meet instance. You will also locally resolve that hostname to your server’s public IP. Jitsi Meet uses both settings when it installs and generates its configuration files.
First, set the system’s hostname to the domain name that you will use for your Jitsi instance. The following command will set the current hostname and modify the /etc/hostname that holds the system’s hostname between reboots:
- sudo hostnamectl set-hostname jitsi.your_domain
Enter your password when prompted. The command that you ran breaks down as follows:
hostnamectl: A utility from the systemd tool suite to manage the system hostname.set-hostname: Sets the system hostname.
Check that the hostname was set with the following command:
- hostname
This command will return the hostname you set with the hostnamectl command:
Outputjitsi.your-domain
Next, you will set a local mapping of the server’s hostname to its public IP address. Do this by opening the /etc/hosts with nano or your favorite text editor:
- sudo nano /etc/hosts
The contents of this file look like the following:
# Your system has configured 'manage_etc_hosts' as True.
# As a result, if you wish for changes to this file to persist
# then you will need to either
# a.) make changes to the master file in /etc/cloud/templates/hosts.debian.tmpl
# b.) change or remove the value of 'manage_etc_hosts' in
# /etc/cloud/cloud.cfg or cloud-config from user-data
#
127.0.1.1 server1 server1
127.0.0.1 localhost
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
Then, add the following line under the 127.0.0.1 localhost line:
...
public_ip jitsi.your_domain
...
For example, if the public IP of your server is 1.2.3.4, the updated file would look like the following:
# Your system has configured 'manage_etc_hosts' as True.
# As a result, if you wish for changes to this file to persist
# then you will need to either
# a.) make changes to the master file in /etc/cloud/templates/hosts.debian.tmpl
# b.) change or remove the value of 'manage_etc_hosts' in
# /etc/cloud/cloud.cfg or cloud-config from user-data
#
127.0.1.1 server1 server1
127.0.0.1 localhost
1.2.3.4 jitsi.your_domain
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
Save and close the file.
Your server now has the hostname and IP address setting Jitsi requires when installed. In the next step, you will open the firewall ports needed by Jitsi and the TLS certificate installer.
Step 2 — Configuring the Firewall
When you followed the Initial Server Setup with Ubuntu 22.04, you enabled the UFW firewall and opened the SSH port. The Jitsi server needs some additional ports open to communicate with the call participants. The TLS installation process also requires a port open to authenticate the certificate registration request.
If you have not yet allowed SSH traffic through UFW, run the following command:
- sudo ufw allow OpenSSH
Next, open the following ports for Jitsi:
80/tcp: Port used in the TLS certificate registration request.443/tcp: Port used for the conference room creation web page.10000/udp3478/udp5349/tcp: Ports that will transmit and receive the encrypted call traffic.
Run the following ufw commands to open these ports:
- sudo ufw allow 80/tcp
- sudo ufw allow 443/tcp
- sudo ufw allow 3478/udp
- sudo ufw allow 5349/tcp
- sudo ufw allow 10000/udp
Check that they were all added with the ufw status command:
- sudo ufw status
You will receive the following output to indicate these ports are open (including OpenSSH):
OutputStatus: active
To Action From
-- ------ ----
OpenSSH ALLOW Anywhere
80/tcp ALLOW Anywhere
443/tcp ALLOW Anywhere
3478/udp ALLOW Anywhere
5349/tcp ALLOW Anywhere
10000/udp ALLOW Anywhere
OpenSSH (v6) ALLOW Anywhere (v6)
80/tcp (v6) ALLOW Anywhere (v6)
443/tcp (v6) ALLOW Anywhere (v6)
3478/udp (v6) ALLOW Anywhere (v6)
5349/tcp (v6) ALLOW Anywhere (v6)
10000/udp (v6) ALLOW Anywhere (v6)
You may see the following inactive status instead of the ports if you have not enabled UFW:
OutputStatus: inactive
If so, you need to enable ufw. Run the following command and answer y when prompted to enable ufw:
- sudo ufw enable
Recheck the status to ensure that the ports are open.
With the ports open, the server is ready for the Jitsi installation, which you will complete in the next step.
Step 3 — Installing Jitsi Meet
You will now add the Jitsi and the Prosody APT repositories to your server. Prosody is an open-source XMPP chat server that Jitsi uses for messaging and admin authentication. You will then install the Jitsi Meet package from its repository, which will ensure that you are always running the latest stable Jitsi Meet package.
First, download the Jitsi GPG key with the curl downloading utility:
- curl https://download.jitsi.org/jitsi-key.gpg.key -o jitsi-key.gpg.key
In this command, -o specifies the name of the file where the downloaded key data will be saved. The apt package manager will use this GPG key to validate the packages you will download from the Jitsi repository.
Next, add the GPG key to your system’s keyring with the following gpg command:
- sudo gpg --output /usr/share/keyrings/jitsi-key.gpg --dearmor jitsi-key.gpg.key
With this gpg command, you use --output to generate a file name to save the keyring in and --dearmor to unpack the key into a format usable by APT.
You will now add the Jitsi repository to your server by creating a new APT sources file that contains the Jitsi repository. Open and create the new file with the following command:
- sudo nano /etc/apt/sources.list.d/jitsi-stable.list
Add this line to the /etc/apt/sources.list.d/jitsi-stable.list file:
deb [signed-by=/usr/share/keyrings/jitsi-key.gpg] https://download.jitsi.org stable/
Save and exit the editor.
Next, you will follow the same steps to add the Prosody package. Download the Prosody GPG key:
- curl https://prosody.im/files/prosody-debian-packages.key -o prosody-debian-packages.key
Then, add the key to your server’s keyring:
- sudo gpg --output /usr/share/keyrings/prosody-keyring.gpg --dearmor prosody-debian-packages.key
Next, open a new sources file for Prosody:
- sudo nano /etc/apt/sources.list.d/prosody.list
Add the following line to the currently empty Prosody sources file:
deb [signed-by=/usr/share/keyrings/prosody-keyring.gpg] http://packages.prosody.im/debian jammy main
Save and exit the editor.
You can now delete the GPG keys that you downloaded as they are no longer needed:
- rm jitsi-key.gpg.key prosody-debian-packages.key
Finally, perform a system update to collect the package list from the new repositories and then install the jitsi-meet package:
- sudo apt update
- sudo apt install jitsi-meet
Press y to confirm the installation of the packages when prompted.
During the installation of jitsi-meet you will be prompted to enter the domain name (for example, jitsi.your-domain) that you want to use for your Jitsi Meet instance.
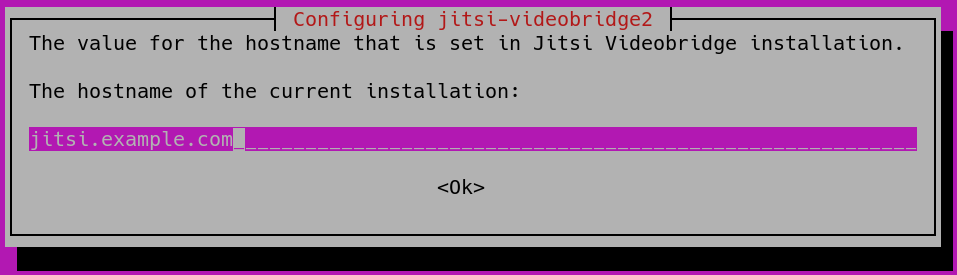
Use the TAB key to move the cursor from the hostname field to highlight the <OK> button. Press ENTER when <OK> is highlighted to submit the hostname.
You will then be shown a new dialog box that asks if you want Jitsi to create and use a self-signed TLS certificate or use an existing one:
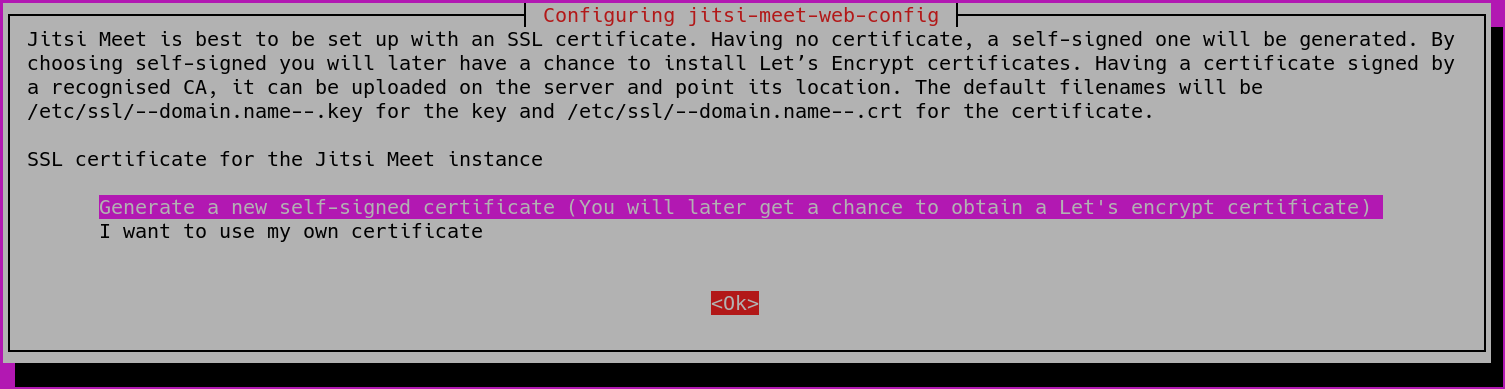
If you do not have a TLS certificate for your Jitsi domain, select the Generate a new self-signed certificate option.
Your Jitsi Meet instance is now installed using a self-signed TLS certificate. You will receive browser warnings if you don’t yet have a TLS certificate, so you will get a signed TLS certificate in the next step.
Step 4 — Obtaining a Signed TLS Certificate
Jitsi Meet uses TLS certificates to encrypt the call traffic so that no one can eavesdrop on your call as it travels over the internet. TLS certificates are the same mechanism used by websites to enable HTTPS-protected pages.
Jitsi uses the certbot utility to obtain and manage free but industry standard and secure TLS certificates. You need to install this utility before Jitsi can get the certificate it needs.
Install certbot with the following command:
- sudo apt install certbot
Press y to confirm the installation of the certbot package when prompted.
Jitsi Meet supplies a script to download a TLS certificate for your domain automatically. Run this certificate installation script provided by Jitsi Meet at /usr/share/jitsi-meet/scripts/install-letsencrypt-cert.sh with the following command:
- sudo /usr/share/jitsi-meet/scripts/install-letsencrypt-cert.sh
The script prints the following information when you run it and asks you to supply an email address:
Output-------------------------------------------------------------------------
This script will:
- Need a working DNS record pointing to this machine(for domain jitsi.your_domain)
- Download certbot-auto from https://dl.eff.org to /usr/local/sbin
- Install additional dependencies in order to request Let’s Encrypt certificate
- If running with jetty serving web content, will stop Jitsi Videobridge
- Configure and reload nginx or apache2, whichever is used
- Configure the coturn server to use Let's Encrypt certificate and add required deploy hooks
- Add command in weekly cron job to renew certificates regularly
You need to agree to the ACME server's Subscriber Agreement
(https://letsencrypt.org/documents/LE-SA-v1.1.1-August-1-2016.pdf)
by providing an email address for important account notifications
Enter your email and press [ENTER]:
This email address will be submitted to the certificate issuer https://letsencrypt.org and will be used to notify you about security and other matters related to the certificate. You must enter an email address here to proceed with the installation.
The script will complete the installation and configuration of an SSL certificate for your Jitsi server without any more user input.
The default configuration for Jitsi Meet is that anyone visiting your Jitsi Meet server homepage can create a new conference room. This default mode will use your server’s system resources to run the conference room and is not desirable for unauthorized users. In the next step, you will update those settings.
Step 5 — Locking Conference Room Creation
You will now configure your Jitsi Meet server to allow only registered users to create conference rooms.
The files you will edit were generated by the installer and configured with your domain name. The variable jitsi.your_domain will be used in place of your domain name in the following examples.
First, open /etc/prosody/conf.avail/jitsi.your_domain.cfg.lua with a text editor:
- sudo nano /etc/prosody/conf.avail/your_domain.cfg.lua
Next, find the line you need to edit in this file using nano’s search function: CTRL+W. Press CTRL+W then enter authentication = "anonymous" into the search field. Press ENTER to run the search. Your search entry should look like the content in the red box below:
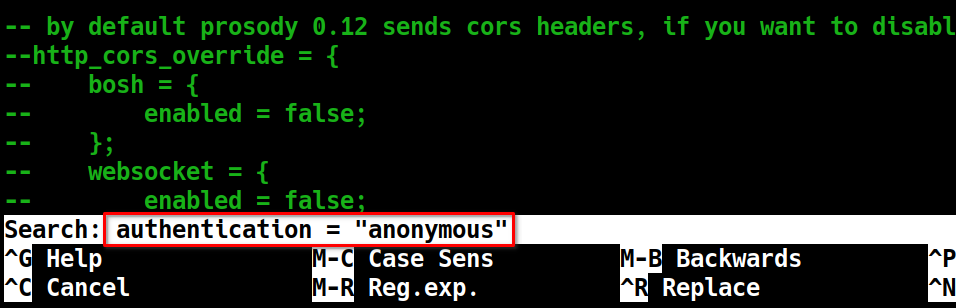
This search will take the cursor to the line that you need to edit. Edit the following line from its current setup:
authentication = "anonymous"
To a new setup:
authentication = "internal_plain"
This configuration tells Jitsi Meet to force username and password authentication before allowing conference room creation by a new visitor.
In the same file, add the following section to the end of the file:
...
VirtualHost "guest.jitsi.your_domain"
authentication = "anonymous"
c2s_require_encryption = false
modules_enabled = {
"bosh";
"ping";
"pubsub";
"speakerstats";
"turncredentials";
"conference_duration";
}
This configuration allows any user to join conference rooms that an authenticated user created. However, the guest must have the unique URL (and an optional password) to enter it.
Here, you added guest. to the front of your domain name. For example, the correct name to put here for jitsi.your_domain is guest.jitsi.your_domain. The guest. hostname is used internally by Jitsi Meet, so you will never enter it into a browser or need a separate DNS record for the guest. hostname.
When finished, save and close the /etc/prosody/conf.avail/jitsi.your_domain.cfg.lua file.
Next, open another configuration file at /etc/jitsi/meet/jitsi.your_domain-config.js with a text editor:
- sudo nano /etc/jitsi/meet/jitsi.your_domain-config.js
Use the search tool CTRL+W again to search for anonymousdomain:, which will take you to the following line:
// anonymousdomain: 'guest.example.com',
Edit this line to look like the following by removing the double slashes // at the start of the line:
anonymousdomain: 'guest.jitsi.your_domain',
You will use the guest.jitsi.your_domain hostname that you used previously. This configuration tells Jitsi Meet what internal hostname to use for the un-authenticated guests. Save and close the file.
Next, create and open /etc/jitsi/jicofo/sip-communicator.properties:
- sudo nano /etc/jitsi/jicofo/sip-communicator.properties
Add the following line to complete the configuration changes:
org.jitsi.jicofo.auth.URL=XMPP:jitsi.your_domain
This configuration points one of the Jitsi Meet processes to the local server that performs the user authentication that is now required. When finished, save and close the file.
Your Jitsi Meet instance is now configured so that only registered users can create conference rooms. After creating a conference room, anyone can join it without being a registered user. All they need is the unique conference room address and an optional password set by the room’s creator.
Now that Jitsi Meet is configured to require authenticated users for room creation, you need to register these users and their passwords. You will use the prosodyctl utility to do this.
Run the following command to add a user to your server:
- sudo prosodyctl register user your_domain password
The user that you add here is not a system user. They will only be able to create a conference room and cannot log in to your server via SSH.
When you run this command, you may see the following warning:
general warn Lua 5.1 has several issues and support is being phased out, consider upgrading
The lua5.1 package is still a required dependency for Prosody and poses no security risk to your system using it. The dependency on lua5.1 will be phased out as Prosody and Jitsi Meet are developed further.
Finally, restart all the Jitsi Meet processes to load the new configuration:
- sudo systemctl restart prosody.service jicofo.service jitsi-videobridge2.service
Your Jitsi Meet server is now fully installed, configured, and running. You will create a new conference room in the final step.
Step 6 - Opening a Conference Room and Inviting Participants
You can now browse to and start using your new Jitsi Meet server. Open your browser and enter your Jitsi domain name (with https) into the address bar.
To start a meeting, press the Start Meeting button on the landing page:
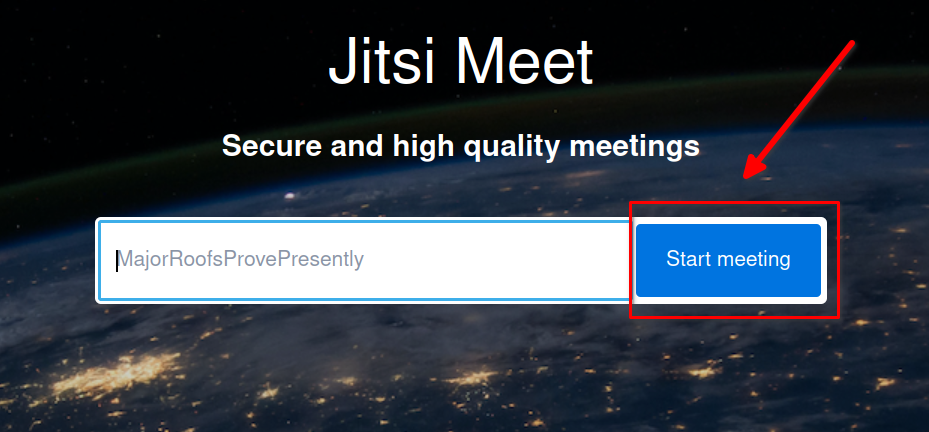
When you click the Start Meeting button, it will begin a new meeting. You will immediately be asked if you are the host (the admin of the meeting) in the following dialog box:
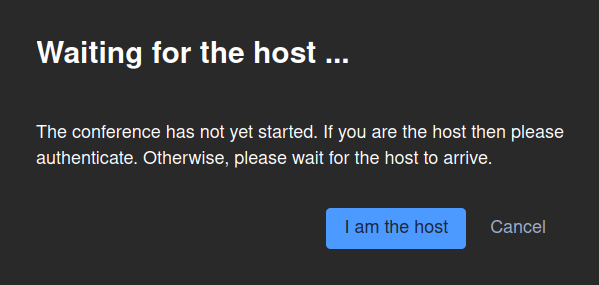
You must click on the I am the host button to proceed. After you click on that button, you will be prompted to enter your admin username and password in the following field:
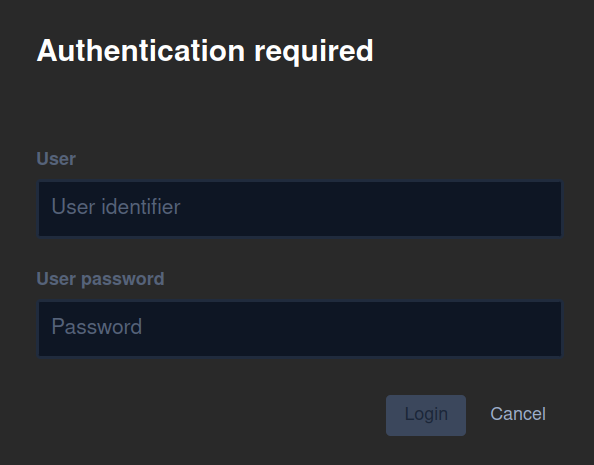
The username and password are the ones that you set in Step 5 with the prosodyctl utility. Enter the username and password and click Login, which will create the new meeting and set you as the moderator.
Now that the meeting is open and running, you can invite participants. Click on the participants icon in the bottom panel:
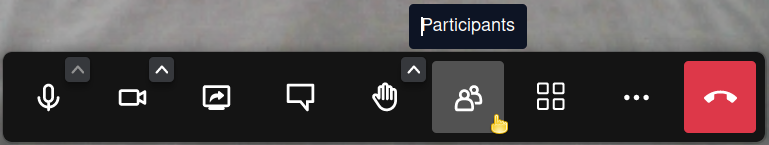
This action opens a right-hand panel. Click on the Invite Someone button:
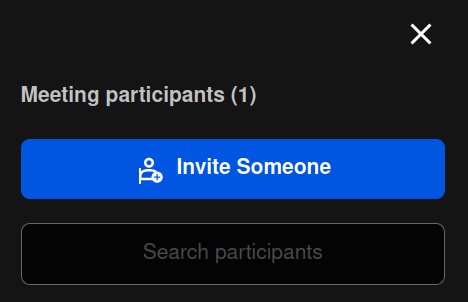
This action will open the Invite more people dialog. Copy the unique URL of the meeting by clicking on the copy icon:
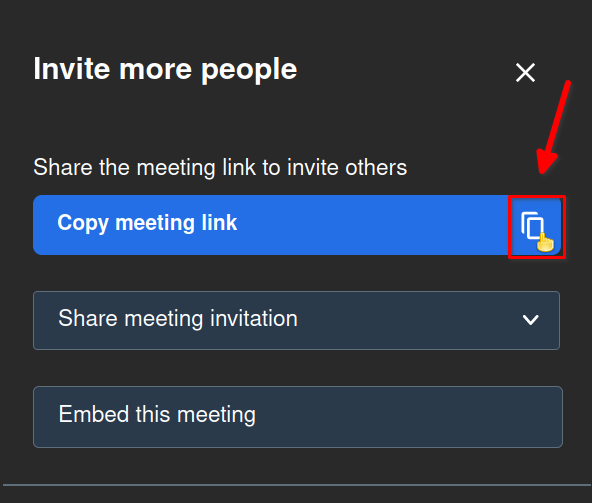
You can now paste the meeting URL into an email or chat program to send to anyone you want to attend the meeting. They will not need a username and password to access the meeting after you have created it.
You can test this yourself after you have created a meeting by opening a new, incognito browser tab and pasting the meeting URL into it. You will be able to join the meeting as a new participant without needing a username and password.
Conclusion
In this article, you deployed a Jitsi Meet server that you can use to host secure and private video conference rooms. You can extend your Jitsi Meet instance with instructions from the Jitsi Handbook. In addition to accessing your conferences in a browser, you can also join conferences with an app from Apple and Google.
Thanks for learning with the DigitalOcean Community. Check out our offerings for compute, storage, networking, and managed databases.
About the author(s)
I have been a Linux Systems Administrator and technical content creator for more than 20 years. I am passionate about using and promoting OSS.
Still looking for an answer?
This textbox defaults to using Markdown to format your answer.
You can type !ref in this text area to quickly search our full set of tutorials, documentation & marketplace offerings and insert the link!
Hello, the file sudo nano /etc/jitsi/jicofo/sip-communicator.properties is not found, I am not the only one who has this question and many people feel sorry to ask
I get the following: jitsi-meet-prosody : Depends: prosody (>= 0.11.7) or prosody-trunk but it is not installable or prosody-0.12 but it is not installable or prosody-0.11 but it is not installable
After i attempt sudo apt install jitsi-meet
Brilliant!! It worked and the Jitsu server is up and running…
However… one issue. I had set up the authentication as per this page. But I don’t get the login window/popup on clicking “start meeting” :-(
Any thoughts/comments please?
Thanks
The “anonymous” authentication setting that is changed toward the beginning of the setup is no longer correct. This is what was installed in my Ubuntu 22.04 /etc/parosody/conf.avail/meet.server.com.cfg.lua on 2023.12.18:
VirtualHost "meet.server.com"
authentication = "jitsi-anonymous" -- do not delete me
-- Properties below are modified by jitsi-meet-tokens package config
-- and authentication above is switched to "token"
--app_id="example_app_id"
--app_secret="example_app_secret"
-- Assign this host a certificate for TLS, otherwise it would use the one
-- set in the global section (if any).
-- Note that old-style SSL on port 5223 only supports one certificate, and will always
-- use the global one.
ssl = {
- Table of contents
- Prerequisites
- Step 1 — Setting the System Hostname
- Step 2 — Configuring the Firewall
- Step 3 — Installing Jitsi Meet
- Step 4 — Obtaining a Signed TLS Certificate
- Step 5 — Locking Conference Room Creation
- Step 6 - Opening a Conference Room and Inviting Participants
- Conclusion
Deploy on DigitalOcean
Click below to sign up for DigitalOcean's virtual machines, Databases, and AIML products.
Become a contributor for community
Get paid to write technical tutorials and select a tech-focused charity to receive a matching donation.
DigitalOcean Documentation
Full documentation for every DigitalOcean product.
Resources for startups and AI-native businesses
The Wave has everything you need to know about building a business, from raising funding to marketing your product.
Get our newsletter
Stay up to date by signing up for DigitalOcean’s Infrastructure as a Newsletter.
New accounts only. By submitting your email you agree to our Privacy Policy
The developer cloud
Scale up as you grow — whether you're running one virtual machine or ten thousand.
Get started for free
Sign up and get $200 in credit for your first 60 days with DigitalOcean.*
*This promotional offer applies to new accounts only.
